How I Automated Code Security Reviews Using Next.js and OWASP APIs
Jun 24, 2025
In an era where cyberattacks are becoming increasingly sophisticated, secure coding is not optional—it's essential. As a full-stack developer, I’ve always prioritized writing clean, scalable code. But when I started building AI-powered developer tools, I realized I needed to shift security from an afterthought to a first-class citizen. That’s when I built an automated code security review system using Next.js, Node.js, and external OWASP security APIs.
In this comprehensive guide, I’ll walk you through how I designed, built, and deployed this tool. Whether you're a solo developer, startup founder, or engineering team lead, this article will help you:
- Understand why automated code security checks are critical.
- Learn how to integrate OWASP APIs into a Next.js app.
- Build a developer-facing UI for real-time security feedback.
- Enable actionable security audits that scale with your codebase.
Let’s dive in.
Why Automating Code Security Reviews Matters
1. Manual Code Reviews Are Not Scalable
Even the best devs miss security flaws during manual reviews. Relying solely on peer review or PR checks means vulnerable code can slip through unnoticed.
2. Shift-Left Security Saves Time and Money
Fixing a security issue in production can cost hundreds of times more than addressing it during development. By automating early checks, you catch vulnerabilities before they become expensive problems.
3. Developer Velocity Improves With Feedback Loops
Developers love instant feedback. Just like linting helps improve code style, automated security checks reduce the cognitive load while coding.
Long-tail keyword tip: "automated code security checks during development" is a common search term by security-conscious devs.
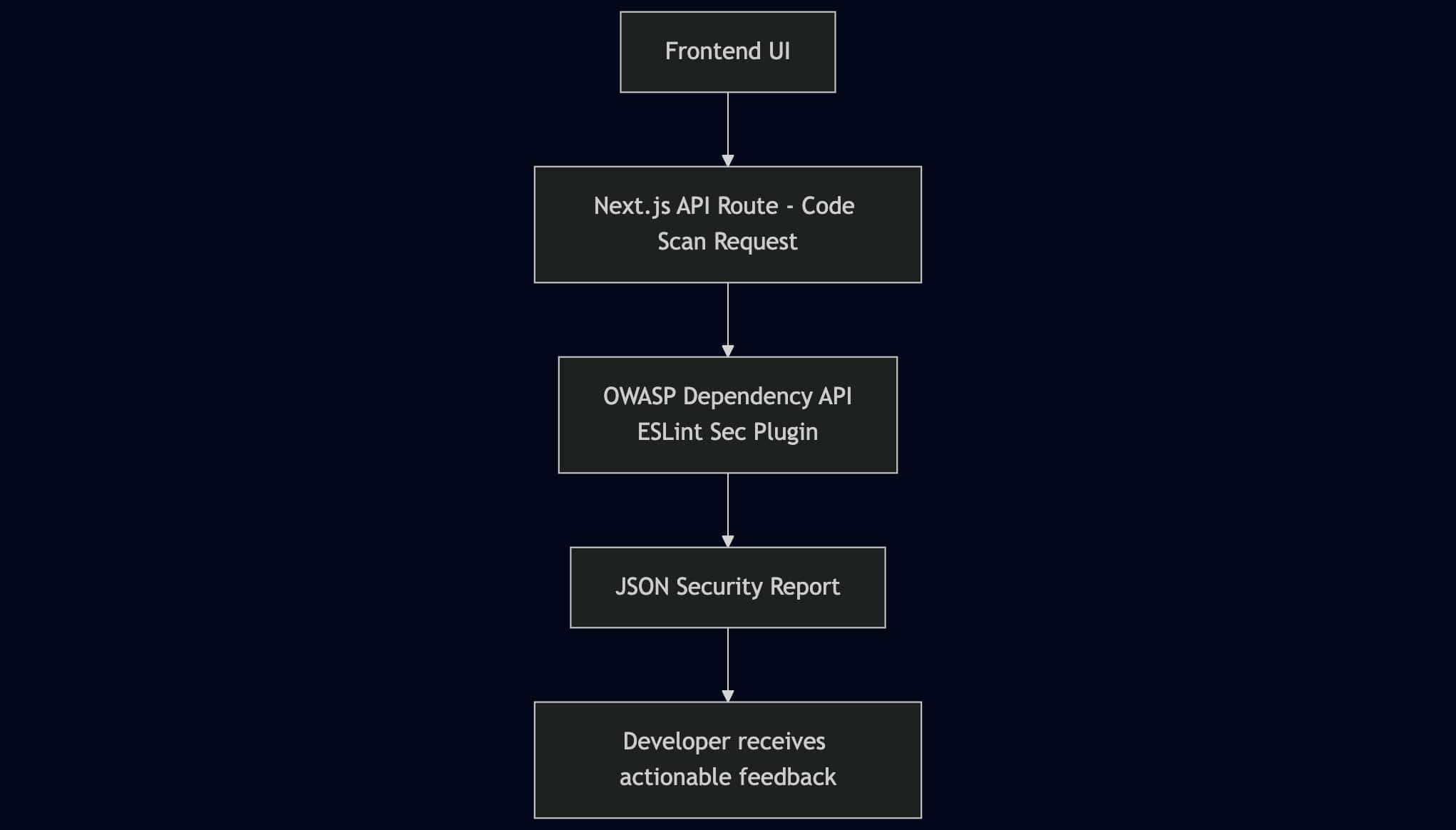
Project Stack and Architecture Overview
To build this system, I used the following technologies:
- Next.js (App Router): For server-side rendering, routing, and API endpoints.
- Node.js: As the backend runtime for invoking APIs and executing secure analysis.
- OWASP Dependency-Check API: To scan code or packages for known vulnerabilities (CVEs).
- ESLint with security plugins: For basic static analysis and secure coding rule enforcement.
- Tailwind CSS: For clean UI and responsive layout.
- Prism.js: For syntax-highlighted code blocks.
Architecture Diagram:
Setting Up OWASP Dependency-Check in a Next.js App
Step 1: Install the Required Tools
npm install eslint eslint-plugin-security
This brings in ESLint with a plugin that enforces best security practices in JavaScript and Node.js apps.
Step 2: Configure ESLint with Security Rules
Create or update your .eslintrc.js file:
module.exports = {
extends: [
'eslint:recommended',
'plugin:security/recommended',
],
plugins: ['security'],
rules: {
// optional overrides
},
};
This static layer helps catch common security mistakes like using eval(), weak regexes, or insecure HTTP headers.
Step 3: Use OWASP Dependency-Check (via API or CLI)
OWASP’s Dependency-Check is a tool that scans dependencies for known vulnerabilities. You can:
Use the Node wrapper
Call a hosted API version (e.g., by setting up your own with Docker)
Example usage:
dependency-check --project MyApp --scan ./src
Or integrate this scan in your Next.js API route (discussed below).
Building a Secure Code Upload API in Next.js
Step 1: Create the /api/security-scan Route
// app/api/security-scan/route.ts
import { NextRequest, NextResponse } from 'next/server';
import { runSecurityScan } from '@/lib/securityScanner';
export async function POST(req: NextRequest) {
const { code } = await req.json();
const report = await runSecurityScan(code);
return NextResponse.json({ report });
}
Step 2: Code Security Scanner Logic
Create a file lib/securityScanner.ts:
import { exec } from 'child_process';
import util from 'util';
const execPromise = util.promisify(exec);
export async function runSecurityScan(code: string) {
// Save code temporarily or run ESLint inline
const { stdout } = await execPromise('eslint temp.js --format json');
return JSON.parse(stdout);
}
Security Tip: Ensure uploaded code is sandboxed (e.g., use VM, Docker, or WASM execution) to avoid RCE.
Frontend: Real-Time Code Analysis UI
Step 1: Build a Code Editor Component
Use a library like react-simple-code-editor + Prism.js:
import Editor from 'react-simple-code-editor';
import Prism from 'prismjs';
<Editor
value={code}
onValueChange={setCode}
highlight={(code) => Prism.highlight(code, Prism.languages.js, 'js')}
padding={10}
style={{ fontFamily: 'monospace', fontSize: 14 }}
/>
Step 2: Submit Code to the Security API
async function handleScan() {
const res = await fetch('/api/security-scan', {
method: 'POST',
headers: { 'Content-Type': 'application/json' },
body: JSON.stringify({ code }),
});
const { report } = await res.json();
setScanReport(report);
}
Step 3: Display Security Results with Severity Labels
{scanReport.map((issue) => (
<div key={issue.ruleId} className="p-2 border mb-2 rounded">
<p><strong>Rule:</strong> {issue.ruleId}</p>
<p><strong>Message:</strong> {issue.message}</p>
<p><strong>Severity:</strong> {issue.severity || 'medium'}</p>
</div>
))}
Tips to Make the Security Audit More Effective
✅ Use Code Sandboxing (VM2 / WASM) Never execute arbitrary code directly. Use sandboxed environments like VM2 or WebAssembly runtimes.
✅ Scan Both Source and Dependencies Combine static code scans (ESLint) with dependency checks (OWASP, Snyk, etc.) to cover both vectors.
✅ Add Severity Scores Map each vulnerability to a CVSS score or color-coded risk level to help prioritize.
✅ Enable CI Integration Hook this into GitHub Actions or GitLab pipelines for automatic PR feedback.
✅ Offer Fix Suggestions Wherever possible, suggest or auto-fix issues—like using parameterized queries instead of string interpolation in SQL.
Challenges and How I Solved Them
❌ Challenge: Scanning Performance Solution: I used async queuing and caching of repeated results. Avoid blocking the UI.
❌ Challenge: False Positives Solution: Allow developers to suppress specific rules with ESLint comments or toggles.
❌ Challenge: Running OWASP Dependency-Check at scale Solution: Containerized it with Docker and exposed it via internal API. Only ran full checks for major PRs.
Future Improvements
- Add support for multiple languages (Python, Go).
- Use LLMs to explain vulnerabilities and suggest fixes.
- Integrate threat intelligence feeds for dynamic CVE checks.
- Export reports to PDF for security auditing.
Conclusion
Automating code security reviews using Next.js, ESLint, and OWASP APIs has drastically improved how I ship software. It enables a developer-first approach to security, catches vulnerabilities early, and fits seamlessly into modern CI/CD pipelines.
Whether you're building your own dev tool, securing your SaaS, or just want better SDLC hygiene, you can use the techniques in this article to:
Detect insecure patterns before they reach production
Speed up development with real-time security feedback
Build user trust with security-first engineering
If you found this guide helpful, bookmark it, share it with your team, and consider adding automated code security scanning to your Next.js apps today. Feel free to reach out if you need help implementing it.
Get in Touch
Want to collaborate or just say hi? Reach out!